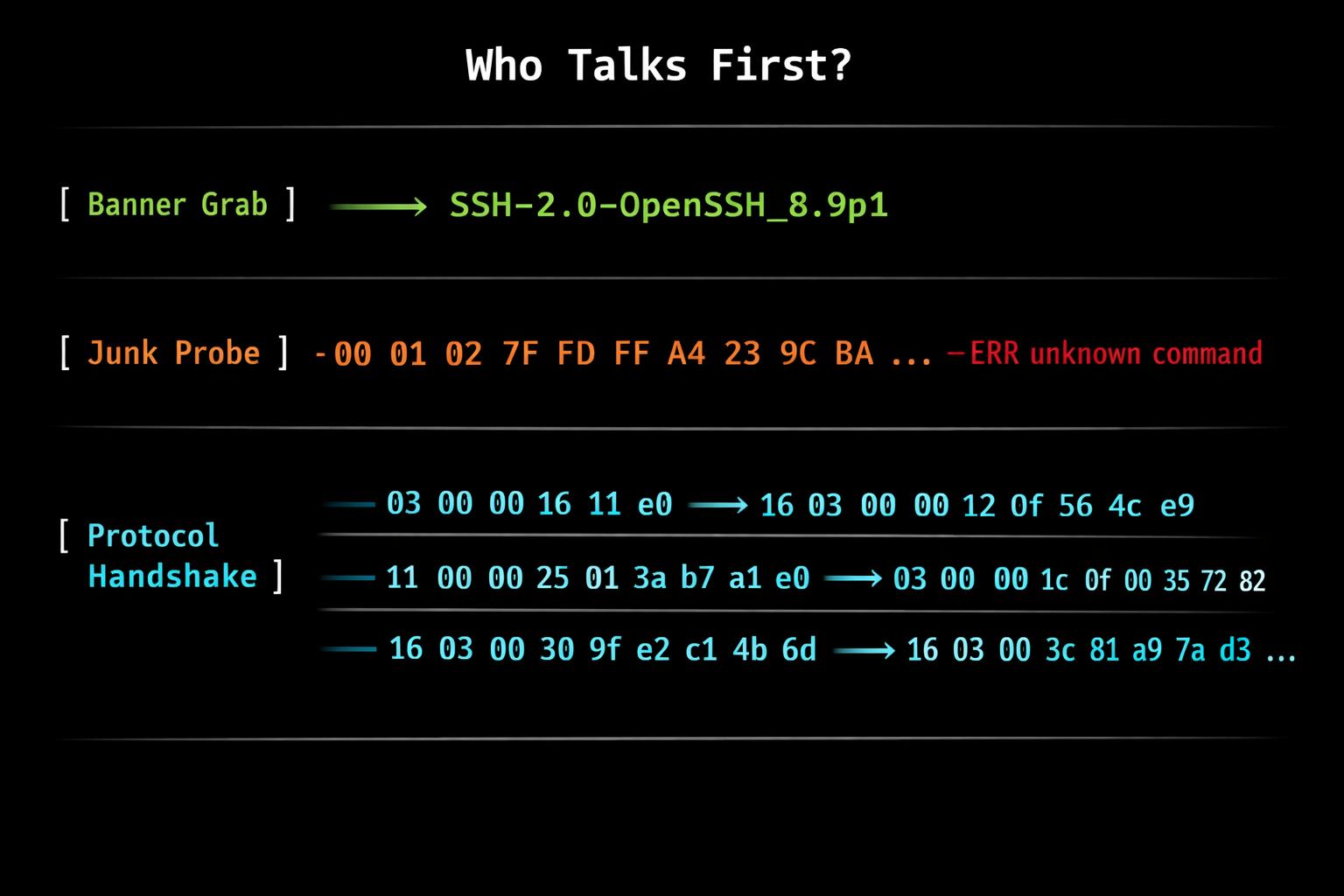
How Internet Scanners Actually Work: The 'Passive' Scanning Myth
A deep dive into how internet-wide scanners like Shodan, Censys, and nmap actually identify services. Spoiler: there's nothing passive about it.
Helping Friends Learn Cybersecurity: Lessons from Teaching Beginners
IDOR Vulnerability: Explanation, Exploitation, and Prevention
In this article, we will explore the Insecure Direct Object Reference (IDOR) vulnerability, a common security vulnerability in web applications that can have significant impacts on data confidentiality, integrity, and availability.
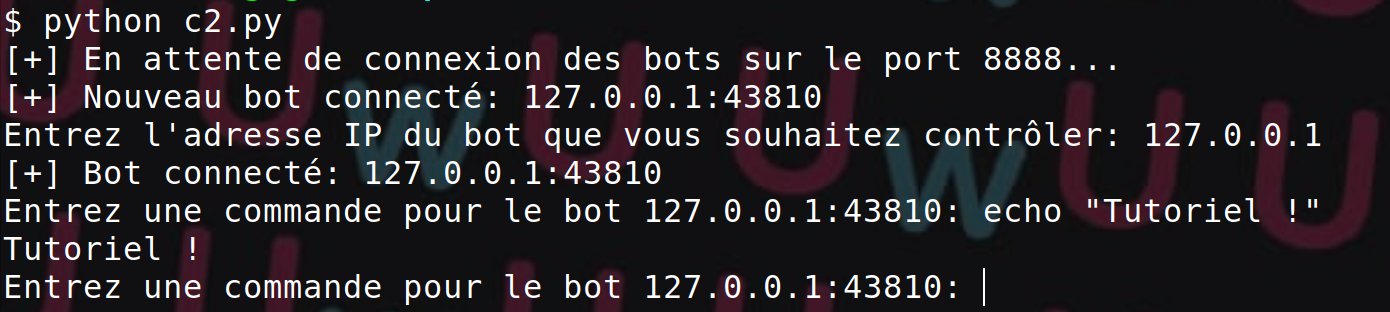
Using Python Sockets for Offensive Security
In this article, we will explore how to use Python sockets in the context of offensive security
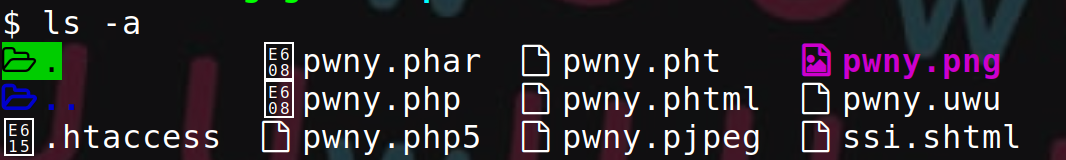
Upload Vulnerabilities: Understanding, Exploiting, and Fixing
This article presents the various variants of the 'upload vulnerability' and how to protect against them.
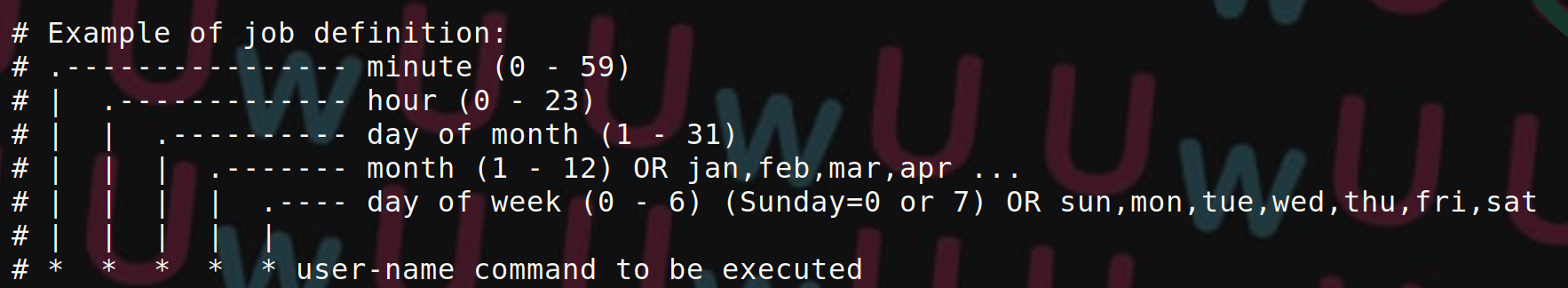
Privilege Escalation on Unix Systems via Crontab
This article demonstrates how to exploit privilege escalation from insecure scheduled tasks.

What is a Command Injection?
This article explains what command injection is, how to exploit it, and how to reduce the risks of this attack.

Configuring an Apache Server with SSL/TLS Hardening
This post explains how to secure an Apache server with SSL/TLS hardening and best practices.