Latest
openDCIM: From SQL Injection to RCE via Config Poisoning
Three chained vulnerabilities in openDCIM turn a missing authorization check into unauthenticated remote code execution on Docker deployments.
Read more →Recent
all →CVE-2026-27743 through CVE-2026-27747: Five Vulnerabilities in SPIP Plugins
Five vulnerabilities across SPIP plugins: two SQL injections, two RCE (one unauth, one auth), and reflected XSS. Same template engine, same mistakes, different entry points.
CVE-2025-71243: AI-Assisted Reversal of SPIP Saisies RCE in 30 Minutes
From VulnCheck advisory to working PoC in 30 minutes. Full AI-assisted reversal of CVE-2025-71243, an unauthenticated PHP code injection in SPIP's Saisies plugin affecting versions 5.4.0 through 5.11.0.
MajorDoMo Revisited: What I Missed in 2023
In 2023 I found CVE-2023-50917 in MajorDoMo. In 2026, AI agents found 8 more bugs I completely missed.
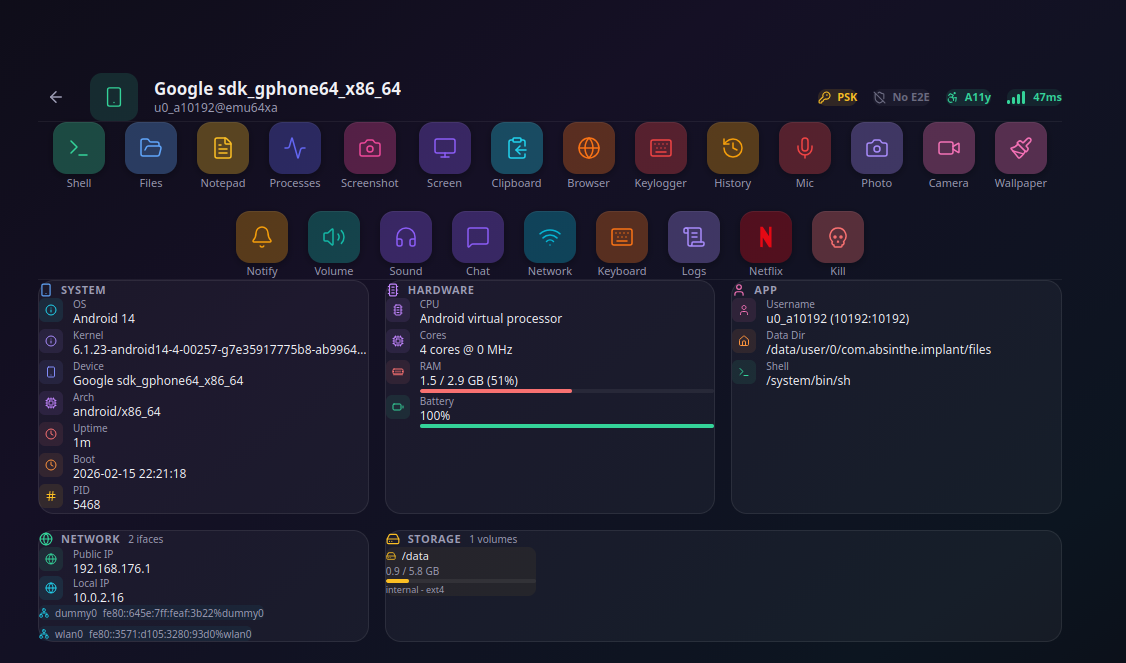
Android's AccessibilityService: A Single Toggle to Total Device Control
How one API designed for disability access became the foundation of a $145M surveillance industry. A proof-of-concept implant demonstrates the full attack chain: silent permission escalation in 2.4 seconds, contextual keylogging, see-through overlays, network toggle, self-hiding persistence, and an embedded Linux terminal with apt - all from a single accessibility toggle, no root required.
LightLLM: Unauthenticated RCE via Pickle Deserialization in WebSocket Endpoints
CVE-2026-26220: A critical unauthenticated RCE vulnerability in LightLLM's PD disaggregation system. Two WebSocket endpoints deserialize binary frames with pickle.loads() without authentication, and the server explicitly refuses to bind to localhost - it's always network-exposed.
manga-image-translator: Unauthenticated RCE via Pickle Deserialization with Nonce Bypass
A critical unauthenticated RCE vulnerability in manga-image-translator. Two FastAPI endpoints deserialize raw HTTP POST bodies with pickle.loads(), and the nonce-based authentication is bypassed because the default value is an empty string - which is falsy in Python.
NEVER GONNA
GIVE YOU UP
You were warned.
