CAF 2023 - IT Administrator Credentials
Table of Contents
In this article, we will explore the step-by-step walkthrough of the Steganography challenge ‘IT Administrator Credentials’ presented at the CTF Cyber Africa Forum 2023.
Challenge File
We have this Word file available: here
Document Analysis
By analyzing the docx document, we can notice that the file is password protected.
Password Hash Extraction
The first reflex when seeing this is to use office2john to generate the hash of the document we have available to attempt a dictionary attack with John The Ripper to read the file content:
$ office2john Administrator_notes.docx | tee -a hash
Administrator_notes.docx:$office$*2013*100000*256*16*504fbe77359c707a81ae26d89f031d59*4a5a4834554b31de39f464c5cd963721*ec8a42ee5c5238b6c93d00a7028548d53ea8e5f3650adbff01a84d5b43c89a62
Password Cracking with John The Ripper
Then:
$ john hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 512/512 AVX512BW 16x / SHA512 512/512 AVX512BW 8x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for statusAfter 20 minutes of execution, I realize that no password has been “cracked”. At this point, I get the idea to generate the rockyou.txt wordlist but in reverse order:
tac /usr/share/wordlists/rockyou.txt > rockyou_inverse.txtReverse Wordlist Attack
By making a new attempt:
$ john hash -w=rockyou_inverse.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 512/512 AVX512BW 16x / SHA512 512/512 AVX512BW 8x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
!a@s#d$f%g555 (Administrator_notes.docx)
1g 0:00:00:04 DONE (2023-04-18 13:52) 0.2188g/s 840.2p/s 840.2c/s 840.2C/s !Toulouse..!adio12
Warning: passwords printed above might not be all those cracked
Use the "--show" option to display all of the cracked passwords reliably
Session completed.We have successfully cracked the document password.
Hidden Content Discovery
Document Content
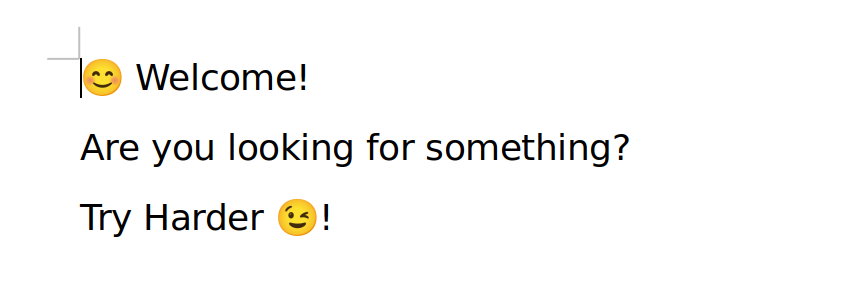
By consulting the document, we have this message:
Steganography Analysis
By chance, I try to do a CTRL+A to see if text might be hidden with white characters.
This attempt was successful since in the footer there is text colored in white, therefore invisible to the naked eye for the reader:
ildfk=YlyvXpJxc;mxpptloa=T@x8(&'#12m
Decryption Process
I get this incomprehensible character string, then I decide to go to CyberChef. Having already the hypothesis that this text strangely resembles text encrypted by substitution, I select the Vigenère Cipher, and I try single-character keys from a to z. By testing the key x, we get the following string:
login=BobyAsMaf;password=W@a8(&'#12p
We have just obtained the administrator’s login and password.
Flag
By respecting the requested flag format:
The flag is CAF_{BobyAsMaf:W@a8(&'#12p}